You’ve probably installed many programs over time on your Windows PC and you probably don’t remember all of them. Generating a list of installed programs in Windows is useful for several reasons:
- Reset or reinstall Windows. A list of installed programs allows you to know what was installed before the reset or reinstall. You can refer to the list once Windows is running again.
- Setting up a new PC. You probably want to install at least some of the same programs you had on your old PC.
- Free up space on your PC. Generating a list of installed programs and reviewing it helps you discover programs you haven’t used in years and don’t need anymore.
Today we’ll cover five ways you can generate a list of installed programs in Windows.
The tools we discuss here do not include license keys and serial numbers for the programs in the list. We’ve previously covered ways to recover serial numbers for Windows programs.
1. List Installed Programs Using PowerShell
PowerShell is a more powerful command line environment than the traditional command prompt. It can perform a lot of the same tasks as the command prompt, but also can be extended and scripted using “cmdlets.”
Don’t be scared off by the power of PowerShell. It can do simple things also, like generate a list of installed programs on your PC.
Open PowerShell by pressing Win + X and selecting Windows PowerShell on the Power User menu.
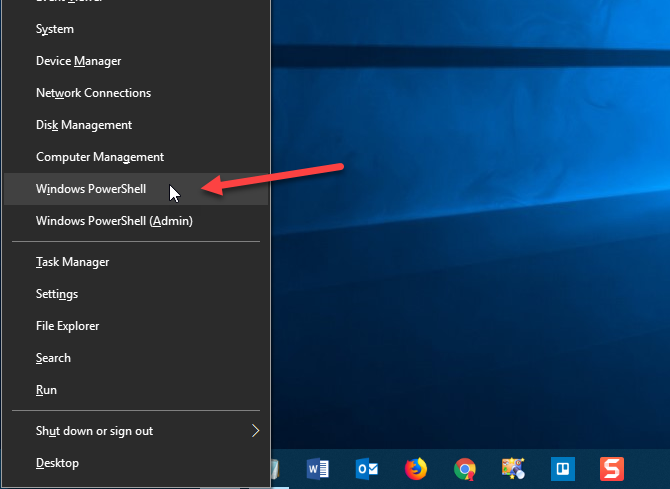
Enter the following command at the prompt and press Enter. You can copy and paste the command from here but replace the path and file name portion (“C:\Users\Lori\Documents\InstalledPrograms\InstalledProgramsPS.txt”) with your own path and the file name you want to use:
Get-ItemProperty HKLM:\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | Select-Object DisplayName, DisplayVersion, Publisher, InstallDate | Format-Table –AutoSize > C:\Users\Lori\Documents\InstalledPrograms\InstalledProgramsPS.txt
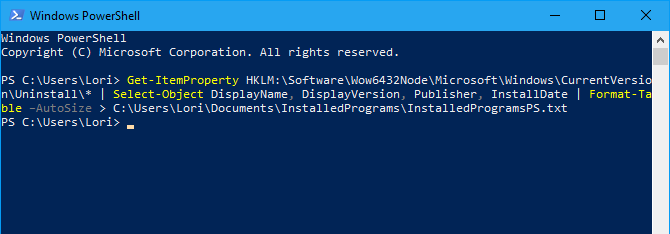
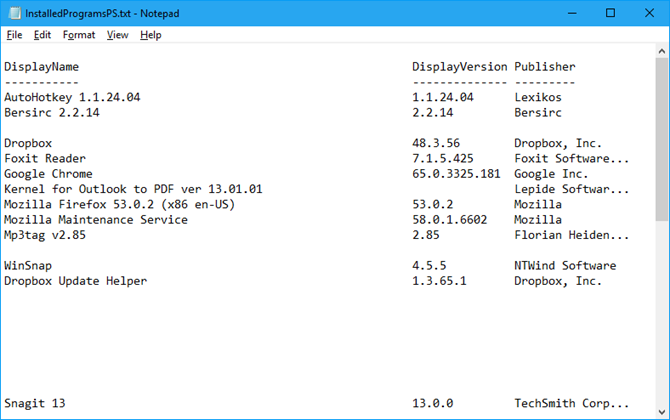
The list contains the name, version, and publisher for each installed program. You may notice several blank lines between some of the items.
2. List Installed Programs Using Command Prompt
If you’re more comfortable using the traditional command prompt rather than PowerShell, you can use the Windows Management Instrumentation Command line tool (WMIC) in the Command Prompt window.
Press Win + R to open the Run dialog box. Then, type “cmd.exe” in the Open box and click OK or press Enter.
If the User Account Control dialog box displays, click Yes to continue.
At the command prompt, type “wmic” and press Enter.
Enter the following line at the wmic:root\cli prompt and press Enter. Replace the path and file name portion (“C:\Users\Lori\Documents\InstalledPrograms\InstalledProgramsWMIC.txt”) with your own path and the file name you want to use:
/output:C:\Users\Lori\Documents\InstalledPrograms\InstalledProgramsWMIC.txt product get name,version
Once you get the wmic:root\cli prompt back, type “exit” and press Enter to return to the normal command prompt.
Type “exit” again and press Enter to close the Command Prompt window.
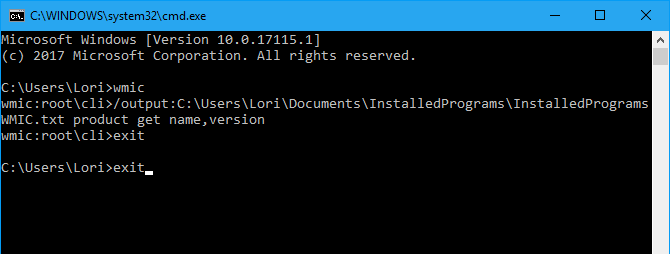
The text file with the name and version for the installed programs on your PC is generated and saved in the location you specified.
3. List Installed Programs Using Control Panel
If you don’t want to type commands to generate a list of installed programs, there are other methods. One way is to view all your installed programs on the Programs and Features screen in the Control Panel.
Type “control panel” in the Search box next to the Start menu. Then, click Control Panel under Best match.
On the Control Panel window, click Uninstall a program under Programs.
If you’re viewing the items by small or large icons, click the Programs and Features item.
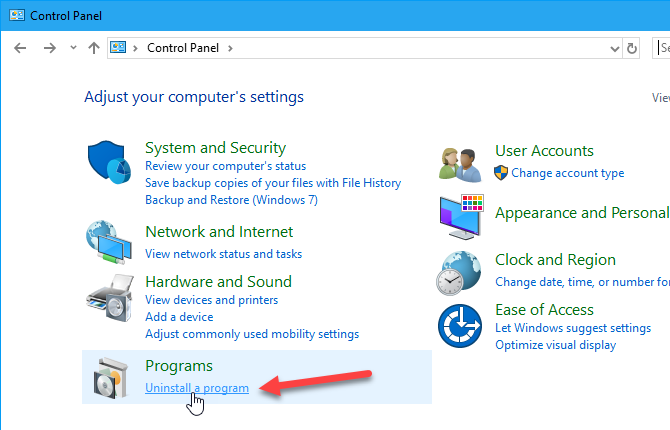
To see all the details for each program in the list on the Uninstall or change a program screen, click the More options arrow on the Change Your View button and select Details.
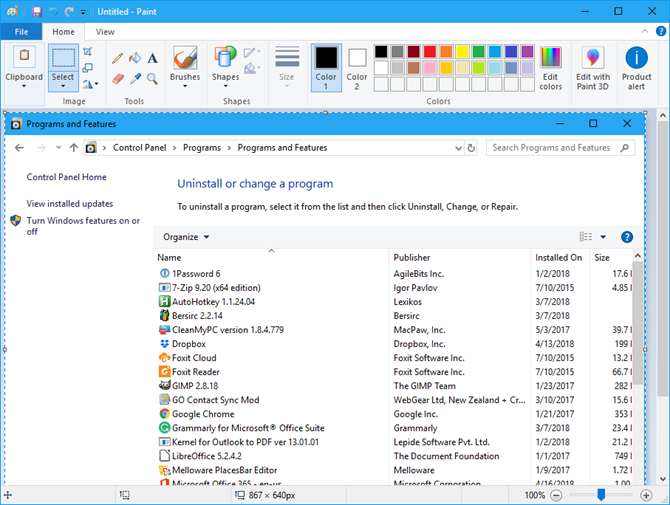
Click on the title bar of the Control Panel window to make sure it’s active. Then, press Alt + Print Screen (or Alt + Fn + Print Screen on some laptops or other devices) to take a screenshot of the window.
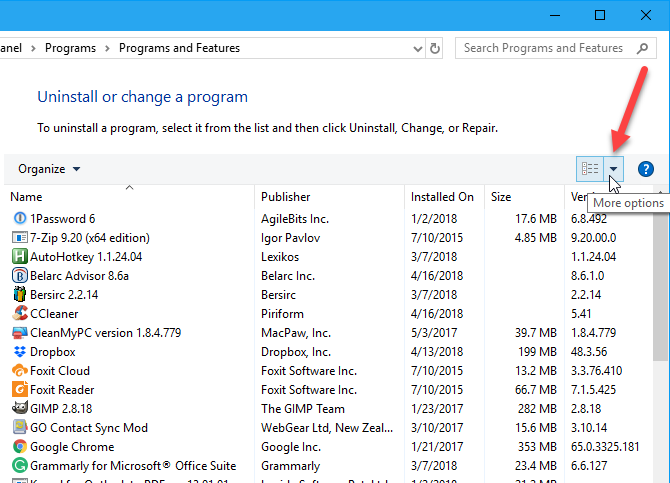
Paste the screenshot into another program like Paint and save the image. In Paint, you can save your screenshot as a PNG, JPEG, BMP, GIF, or other formats.
Depending on how many programs are installed, you may need to take multiple screenshots of the Control Panel window, scrolling down for each one to capture the next part of the list. If this is the case, you may want to paste each image directly into a word processor like Word to save them all in one file.
4. List Installed Programs Using CCleaner
CCleaner is a Windows program that allows you to easily clean up and free up space on your PC. You can delete temporary files, your browsing and download history, and recent documents lists in some programs.
The program also includes an uninstaller tool, which generates a list of installed programs on your PC. This list can be saved to a text file.
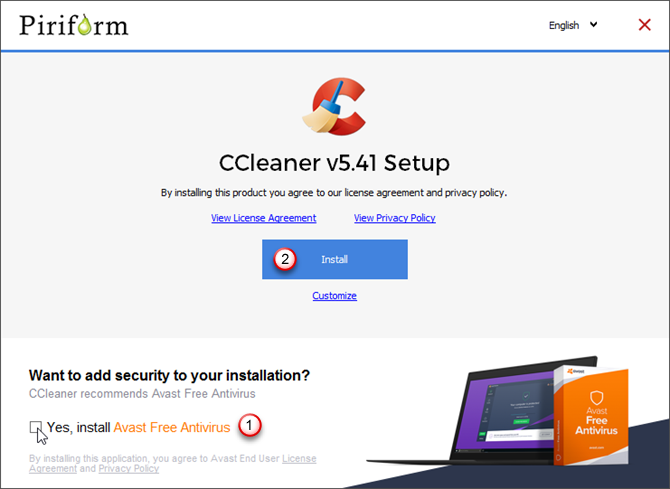
Download CCleaner and install it. Be aware that Avast Free Antivirus will be automatically installed while installing CCleaner unless you uncheck the Yes, install Avast Free Antivirus box before clicking Install to begin the installation.
Open CCleaner and hit the Tools button on the gray sidebar on the left. Then, make sure that Uninstall is selected to the right of that sidebar.
Click the blue Save to text file button in the lower-right corner.
On the Save As dialog box, navigate to the folder where you want to save the installed programs list, enter a File name and click Save.
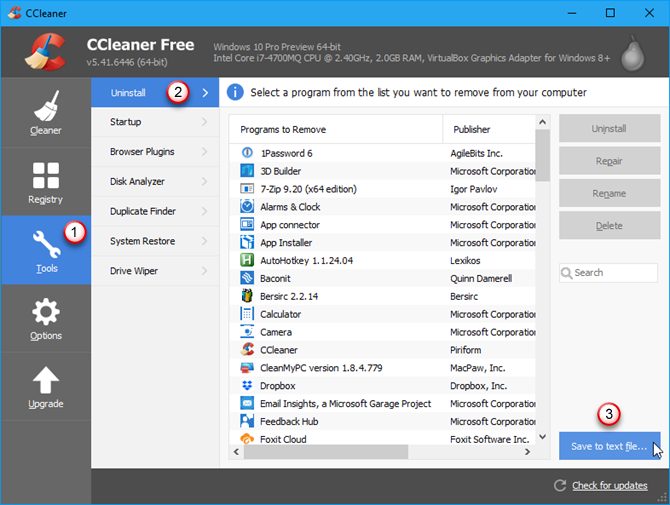
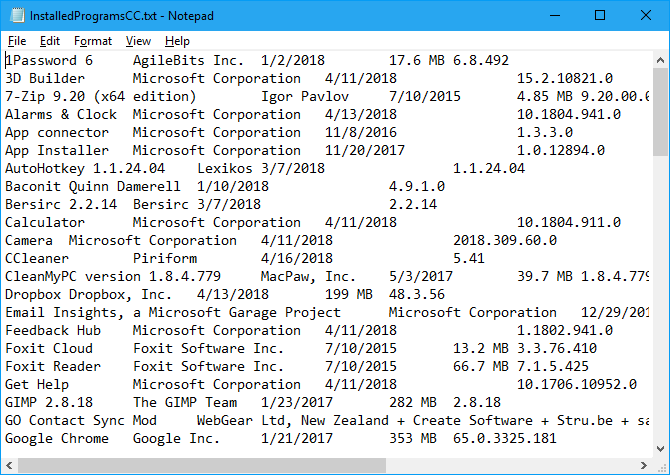
The list of installed programs includes the company, date installed, size, and version number for each program.
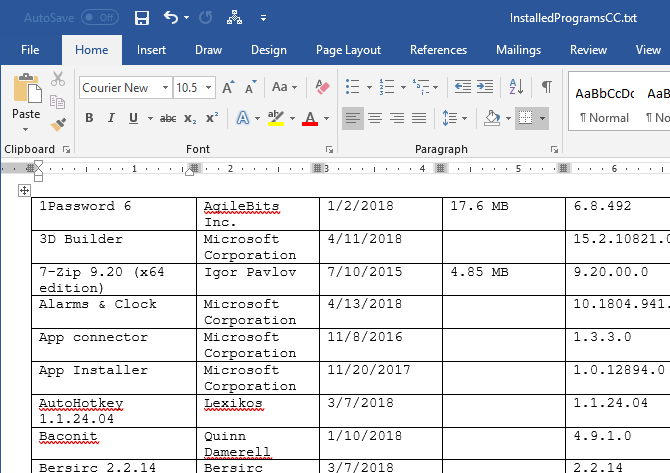
The text is tab-delimited, which makes it somewhat hard to read in a text editor. You can import the text from this file into Word or Excel to make it easier to read. Read on to learn how to convert this data into a table in Word or into a worksheet in Excel.
Remember that if you save your list of programs in Word or Excel, you must install that program on the newly installed or reset Windows system before you can access your list. Or use online document viewers. The next two tips show you how to format the text list into neat tables.
Tip: Convert Your List of Programs Into a Word Table
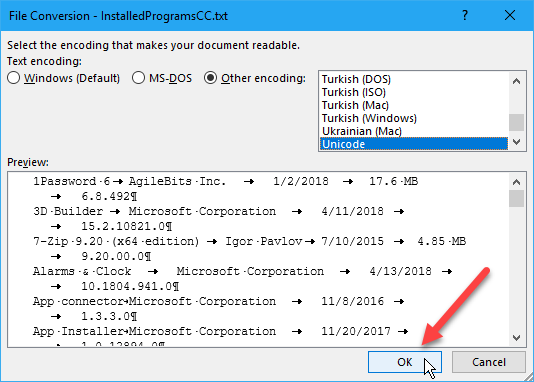
To convert your list to a table in Word, open the text file you saved in Word. The File Conversion dialog box displays before the file opens, showing how the text will look in the Preview box.
Accept the default settings and click OK.
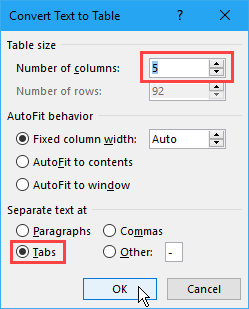
Select the text you want to convert to a table. Then, on the Insert tab, click Table and select Convert Text to Table.
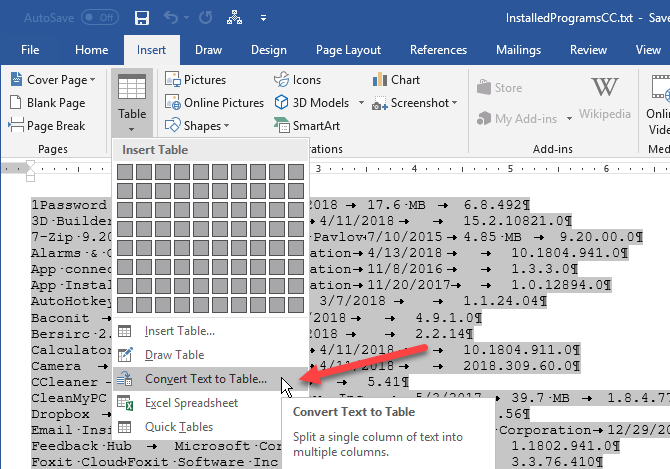
Make sure the number of columns is 5 and that Tabs is selected under Separate text at.
Click OK to continue with the conversion.
Format the table any way you want. Be sure to save the Word file to an external or network drive so you’ll have access to it once you reinstall or reset Windows.
Tip: Convert Your List of Programs Into an Excel Worksheet
If you’d rather have your list of programs in Excel, here’s how to convert the list to an Excel worksheet.
First, we recommend you make a copy of the original text file. Change the extension on the copied file from .txt to .csv and open the .csv file in Excel.
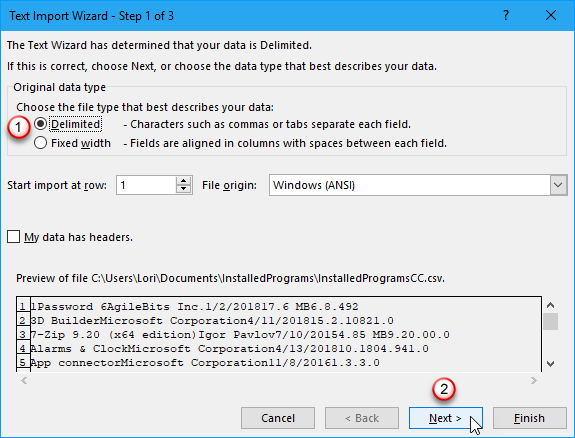
On the first screen of the Text Import Wizard dialog box, make sure Delimited is selected under Choose the file type that best describes your data.
Accept the defaults for the rest of the settings on this screen and click Next.
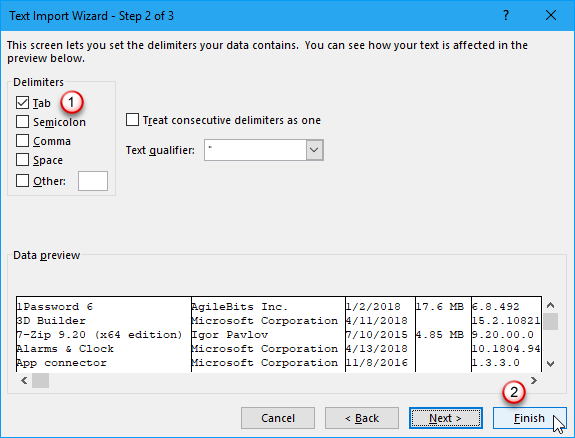
On the second screen, make sure Tab is checked under Delimiters.
Click Finish. For our purpose, we don’t need to do Step 3.
Your list of programs is imported into columns on a worksheet in Excel, making it easier to read. Be sure to save the Excel file to an external or network drive so you’ll have access to it once you reinstall or reset Windows.
5. List Installed Programs Using Geek Uninstaller
Geek Uninstaller is a free, portable Windows program used to thoroughly uninstall programs, including all leftovers. The program will also forcefully remove stubborn or broken programs. You can use Geek Uninstaller to generate and save a list of installed programs on your PC.
Download Geek Uninstaller. The program is portable. Simply unzip the downloaded file into a folder on your PC and run the EXE file.
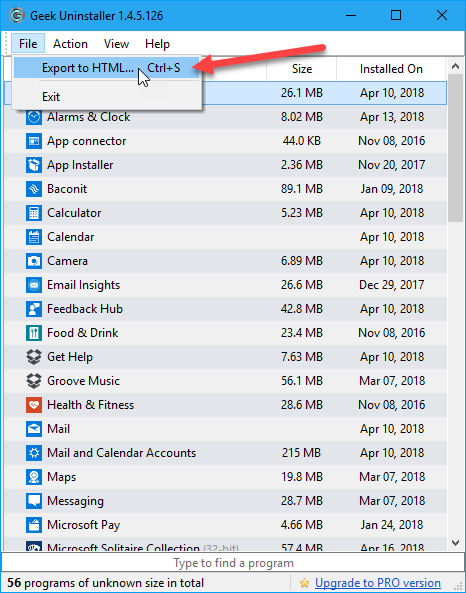
A list of installed programs displays on the Geek Uninstaller main window. To save this list to an HTML file, open Geek Uninstaller and go to File > Export to HTML, or press Ctrl + S.
On the Save As dialog box, navigate to the folder where you want to save the installed programs list, enter a File name and click Save.
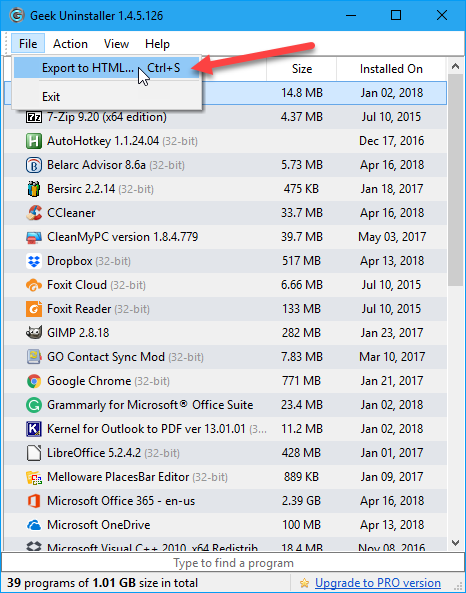
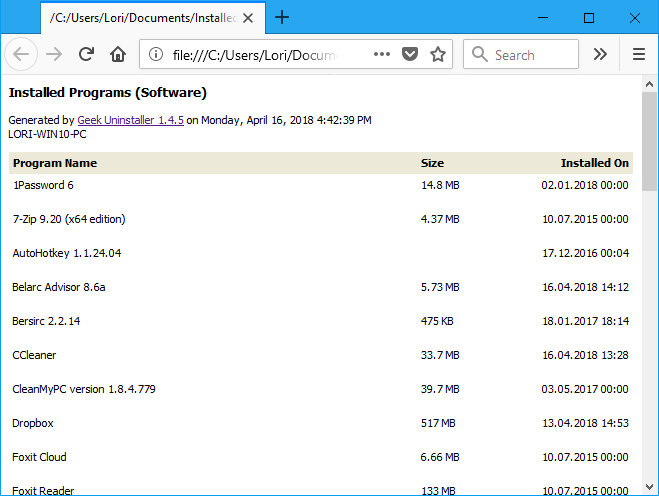
The HTML file automatically opens in the default browser once it’s saved. The list includes the name and size of each program and the date on which the program was installed.
If you’re using a browser like Firefox, Chrome, or Vivaldi, hit Ctrl + S to save the Installed Programs HTML page to a location you choose with a custom file name. You can save it to your local hard drive but be sure you transfer the file to an external or network drive before reinstalling Windows. Other browsers may have a different shortcut or option for saving HTML files.
Geek Uninstaller also allows you to display a list of apps installed from the Windows Store. Go to View > Windows Store Apps.
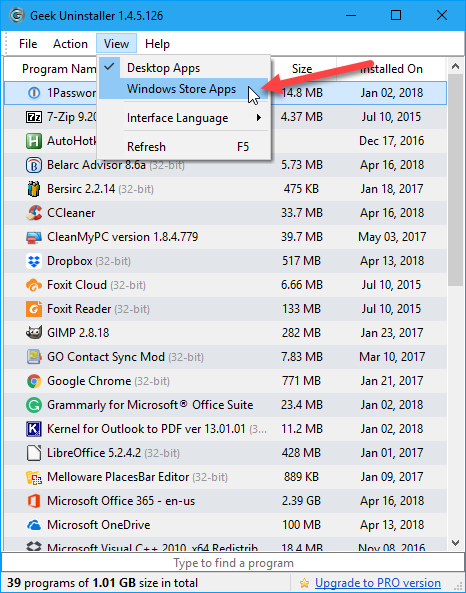
All the apps installed on your PC from the Windows Store display. You can export this list to an HTML file the same way you did for the list of regular Windows programs.
Store the Generated App Lists on External Media
You might have noticed that each of the methods we mentioned here produces a slightly different list of programs. So you might want to use more than one method and keep each separate list.
Remember to store your lists of programs on an external or network drive so you have access to it after reinstalling Windows. When you reset (instead of reinstalling) Windows 10, programs are removed but your data is preserved. No matter what the situation, it’s a good idea to back up your lists when backing up your data.